8 security patches for PeopleSoft in October 2022 CPU
Oracle just released the Critical Patch Updates (CPU) for October 2022 and there are 8 new security patches for Oracle PeopleSoft applications.
You should review these patches and consider applying to your PeopleSoft application, if it’s impacted by any of these. Oracle strongly recommends that every critical patch must be applied to the impacted application as soon as possible.
October 2022 CPU security patches impacts PeopleTools 8.58, 8.59 & also 8.60 which was just released.
If you are on an older PeopleTools, it doesn’t mean that your PeopleSoft application isn’t impacted. Oracle strongly recommends customers to upgrade to a PeopleTools version that is currently supported by Oracle.
Not sure, if your PeopleTools version is still supported by Oracle or want to know how long will it be supported for? Check out the PeopleTools Support policy.
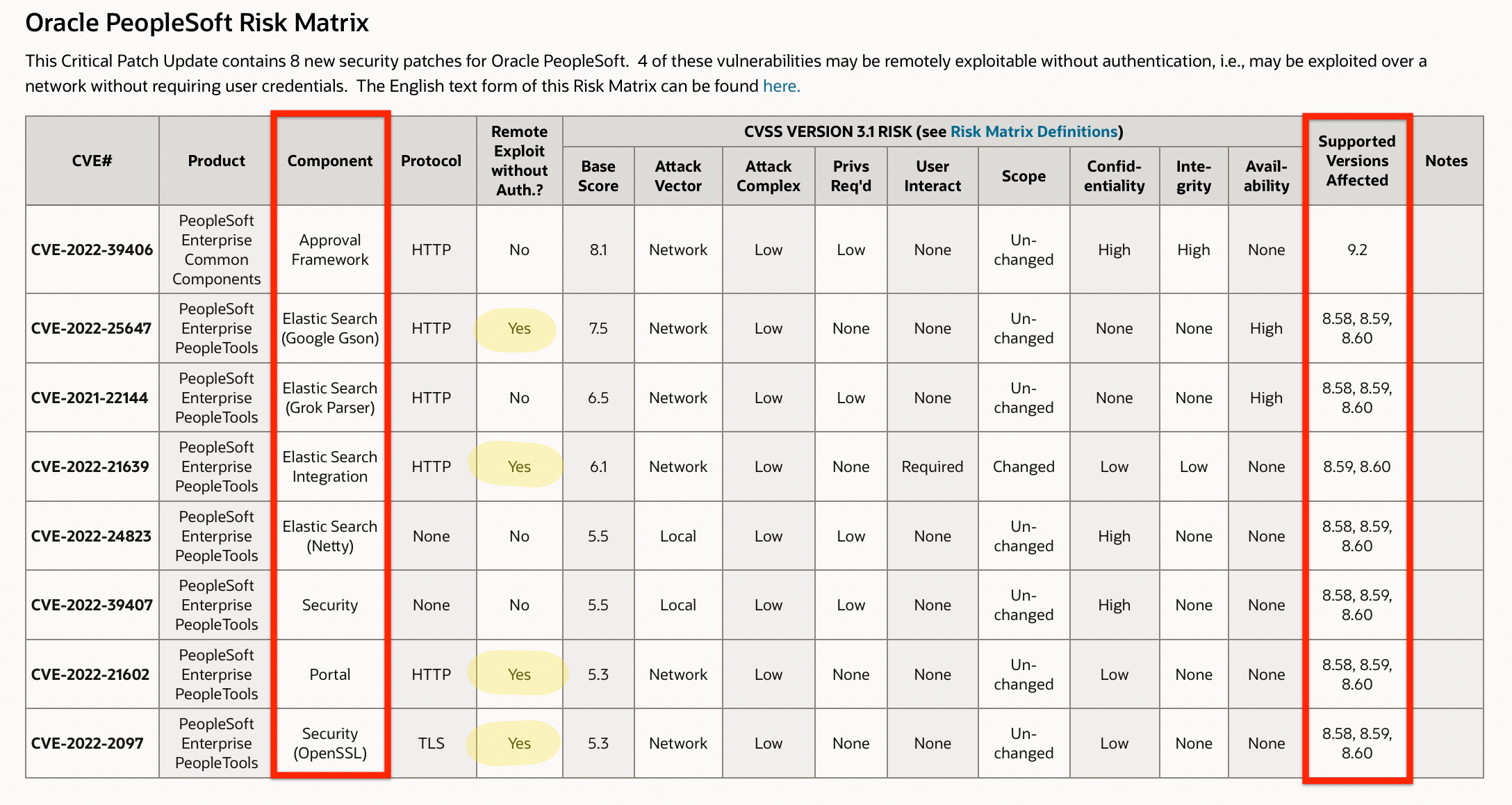
Here are a few highlights for PeopleSoft applications based on Oracle PeopleSoft Risk Matrix.
- Total 8 security patches impacting PeopleSoft applications.
- 4 of these vulnerabilities can be remotely exploited without the authentication.
- 4 impact Elastic Search, 2 impact Security, 1 impact Portal and 1 impact Approval Framework.
- PeopleTools Impacted
- PeopleTools 8.58 – 6 patches
- PeopleTools 8.59 – 7 patches
- PeopleTools 8.60 – 7 patches
The CVSS Base Score is an assessment of risk defined by the Common Vulnerability Scoring Standard (CVSS). The CVSS Base Score is a numeric value between 0.0 and 10.0 which indicates the relative severity of the vulnerability, where 10.0 represents the highest severity. Each risk matrix is ordered using this value, with the most severe vulnerability at the top of each risk matrix.
As per NVD (National Vulnerability Database) which is maintained by the NIST (National Institute of Standards and Technology), U.S Department of Commerce, below are the details of these CVE.
CVE-2022-39406 Detail
Impacts: PeopleSoft 9.2
Component: Approval Framework
Description
Vulnerability in the PeopleSoft Enterprise Common Components product of Oracle PeopleSoft (component: Approval Framework). The supported version that is affected is 9.2. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise PeopleSoft Enterprise Common Components.
Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all PeopleSoft Enterprise Common Components accessible data as well as unauthorized access to critical data or complete access to all PeopleSoft Enterprise Common Components accessible data. CVSS 3.1 Base Score 8.1 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:N).
CVE-2022-25647 Detail
Impacts: PeopleTools 8.58, 8.59 & 8.60
Component: Elastic Search
Current Description
The package com.google.code.gson:gson before 2.8.9 are vulnerable to Deserialization of Untrusted Data via the writeReplace() method in internal classes, which may lead to DoS attacks.
CVE-2021-22144 Detail
Impacts: PeopleTools 8.58, 8.59, 8.60
Component: Elastic Search (Grok Parser)
Current Description
In Elasticsearch versions before 7.13.3 and 6.8.17 an uncontrolled recursion vulnerability that could lead to a denial of service attack was identified in the Elasticsearch Grok parser. A user with the ability to submit arbitrary queries to Elasticsearch could create a malicious Grok query that will crash the Elasticsearch node.
CVE-2022-21639 Detail
Impacts: PeopleTools 8.59 & 8.60
Component: Elastic Search Integration
Description
Vulnerability in the PeopleSoft Enterprise PeopleTools product of Oracle PeopleSoft (component: Elastic Search Integration). Supported versions that are affected are 8.59 and 8.60. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise PeopleSoft Enterprise PeopleTools.
Successful attacks require human interaction from a person other than the attacker and while the vulnerability is in PeopleSoft Enterprise PeopleTools, attacks may significantly impact additional products (scope change). Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of PeopleSoft Enterprise PeopleTools accessible data as well as unauthorized read access to a subset of PeopleSoft Enterprise PeopleTools accessible data.
CVE-2022-24823 Detail
Impacts: PeopleTools 8.58, 8.59 and 8.60
Component: Elastic Search (Netty)
Current Description
Netty is an open-source, asynchronous event-driven network application framework. The package `io.netty:netty-codec-http` prior to version 4.1.77.Final contains an insufficient fix for CVE-2021-21290. When Netty’s multipart decoders are used local information disclosure can occur via the local system temporary directory if temporary storing uploads on the disk is enabled. This only impacts applications running on Java version 6 and lower.
Additionally, this vulnerability impacts code running on Unix-like systems, and very old versions of Mac OSX and Windows as they all share the system temporary directory between all users. Version 4.1.77.Final contains a patch for this vulnerability. As a workaround, specify one’s own `java.io.tmpdir` when starting the JVM or use DefaultHttpDataFactory.setBaseDir(…) to set the directory to something that is only readable by the current user.
CVE-2022-39407 Detail
Impacts: PeopleTools 8.58, 8.59, 8.60
Component: Security
Description
Vulnerability in the PeopleSoft Enterprise PeopleTools product of Oracle PeopleSoft (component: Security). Supported versions that are affected are 8.58, 8.59 and 8.60. Easily exploitable vulnerability allows low privileged attacker with logon to the infrastructure where PeopleSoft Enterprise PeopleTools executes to compromise PeopleSoft Enterprise PeopleTools. Successful attacks of this vulnerability can result in unauthorized access to critical data or complete access to all PeopleSoft Enterprise PeopleTools accessible data.
CVE-2022-21602 Detail
Impacts: PeopleTools 8.58, 8.59 & 8.60
Component: Portal
Description
Vulnerability in the PeopleSoft Enterprise PeopleTools product of Oracle PeopleSoft (component: Portal). Supported versions that are affected are 8.58, 8.59 and 8.60. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise PeopleSoft Enterprise PeopleTools. Successful attacks of this vulnerability can result in unauthorized read access to a subset of PeopleSoft Enterprise PeopleTools accessible data.
CVE-2022-2097 Detail
Impacts: PeopleTools 8.58. 8.59 & 8.60
Component: Security (Open SSL)
Description
AES OCB mode for 32-bit x86 platforms using the AES-NI assembly optimized implementation will not encrypt the entirety of the data under some circumstances. This could reveal sixteen bytes of data that was preexisting in the memory that wasn’t written.
In the special case of “in place” encryption, sixteen bytes of the plaintext would be revealed. Since OpenSSL does not support OCB based cipher suites for TLS and DTLS, they are both unaffected. Fixed in OpenSSL 3.0.5 (Affected 3.0.0-3.0.4). Fixed in OpenSSL 1.1.1q (Affected 1.1.1-1.1.1p).
You can learn more about Oracle CPU patches here.
If you are interested to learn more about CVE (Common Vulnerabilities and exposures) patches and how these are scored, please refer to this article and this article.

